A lot of companies would love to secure a contract with a government agency as large as the U.S. Department of Defense (DoD), but many don’t realize it comes with a mandatory compliance requirement: CMMC certification. Becoming CMMC certified is no small feat, especially for organizations without a strong cybersecurity practice—which is kind of the point.
The DoD developed the Cybersecurity Maturity Model Certification (CMMC) to protect its data and its interests. More specifically, the CMMC was designed to protect Controlled Unclassified Information (CUI), which is information that is not classified and has the potential to cause harm to the DoD if it were disclosed to unauthorized individuals. Examples of CUI include:
- Technical data about weaponry, military tactics, and foreign intelligence
- Engineering drawings and blueprints about weaponry, aircraft, and buildings
- Source code for proprietary software, systems, and specifications
- Financial data regarding budgets, contracts, and investigations
The DoD is rightly cracking down on cybersecurity attack vectors. According to IBM, it took an average of 206 days before a data breach was discovered in 2022. The CMMC is a model of necessity, national security, and proactivity.
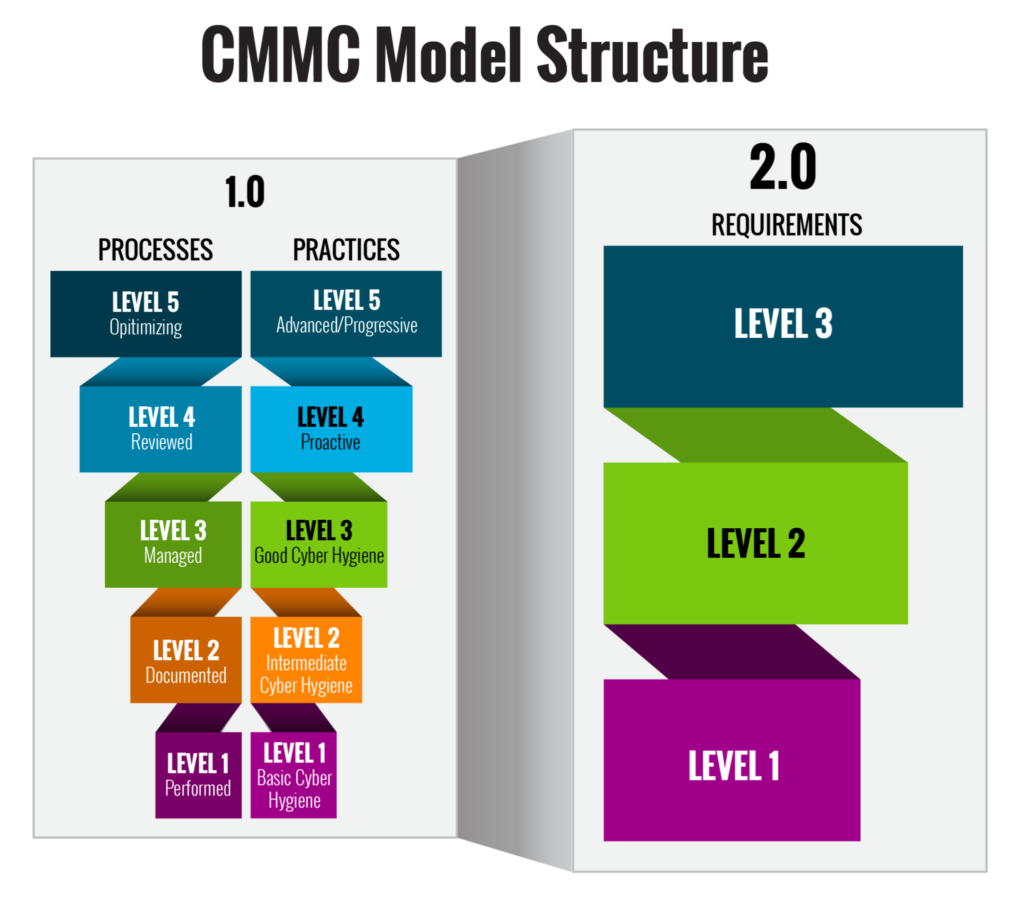
Overview of the CMMC 2.0 model, source
What is the CMMC and how does it work?
The CMMC is a cybersecurity framework developed by the DoD. In addition to protecting CUI, it also protects Federal Contract Information (FCI) that’s shared with the DoD’s contractors and subcontractors on projects and via acquisition.
CMMC 1.0 (2018)
As of this writing, there are two versions of the CMMC, known as CMMC 1.0 and CMMC 2.0. CMMC 1.0 was released in September 2018 and was finalized in December 2019 as a five-level maturity framework covering a wide range of cybersecurity topics, including:
- Asset management
- Personnel security
- Physical security
- Information security
- Systems and communications security
- Incident response
The five levels of CMMC 1.0 are as follows:
- Level 1: Basic. These organizations demonstrate a basic understanding of cybersecurity with basic security controls.
- Level 2: Repeatable. These organizations demonstrate a repeatable approach to cybersecurity with more advanced security controls.
- Level 3: Managed. These organizations demonstrate a managed approach to cybersecurity with comprehensive security controls.
- Level 4: Optimizing. These organizations demonstrate an optimizing approach to cybersecurity with an eye toward constantly improving security.
- Level 5: Advanced. These organizations demonstrate an advanced approach to cybersecurity with demonstrable leadership in their respective industries.
CMMC 2.0 (projected for 2025)
The CMMC 2.0 framework is still under active development, but is expected to be finalized by 2025. The requirements are complete enough for organizations to begin preparing for compliance today, in 2023.
CMMC 2.0 is a three-level framework, as opposed to CMMC 1.0’s five levels. It is primarily focused on CUI instead of CUI and FCI. CMMC 2.0’s three levels are described as follows:
- Level 1: Foundational. These organizations demonstrate foundational capabilities in handling and protecting lower-risk CUI. This is the same as CMMC 1.0 Level 1.
- Level 2: Advanced. These organizations demonstrate advanced capabilities in handling and protecting sensitive CUI that can have a material impact on the DoD. This is the same as CMMC 1.0 Level 3.
- Level 3: Expert. These organizations demonstrate expert capabilities in handling and protecting mission-critical CUI. This is the same as CMMC 1.0 Level 5.
There are several reasons for CMMC 2.0 to supersede CMMC 1.0. The main issue comes down to complexity and difficulty in understanding it. Some believe CMMC 1.0 to be too open to interpretation and potentially easy to misinterpret, making it difficult for organizations to consistently assess their compliance. CMMC 2.0 is more focused and less broad than its predecessor and is required for any organization working with CUI, regardless of their affiliation with the DoD.
Benefits of implementing CMMC
Every organization can benefit from a stronger cybersecurity posture with compliant access controls. CMMC is just one way of doing so that is specific to the needs of the DoD. Here are some of the benefits of CMMC certification:
- Increased cybersecurity posture: CMMC certification helps organizations with a roadmap for best practices.
- Enhanced compliance: CMMC certification helps organizations demonstrate compliance with a variety of cybersecurity regulations, including NIST SP 800-53 and DFARS 252.204-7012.
- Improved risk management: CMMC certification helps organizations protect their assets and operations by identifying and mitigating cybersecurity risks.
- Increased confidence from customers: CMMC certification bolsters the confidence of an organization’s customers, especially at the higher levels of maturity.
Who should be CMMC certified?
The following types of organizations should consider getting CMMC certified:
- Organizations that directly or indirectly work with the DoD must be certified, including contractors, subcontractors, and suppliers.
- Organizations that handle CUI, whether working directly or indirectly with the DoD. CMMC 2.0 mandates certification whereas CMMC 1.0 does not, and includes any company that stores, processes, or transmits CUI.
- Any organization interested in improving their cybersecurity posture, regardless of whether they work with the DoD or handle CUI.
Becoming CMMC certified can be done independently, but is best done via a third-party certifying partner that’s accredited by the CMMC Accreditation Board (CMMC-AB). CMMC 2.0 allows for self-certification only at the Foundational level. Levels 2 and 3 require third-party assessment.
Challenges and misconceptions about CMMC certification
Getting CMMC certified is a challenging and complex endeavor that can be confusing and lead to misconceptions. It requires organizations to implement a wide range of cybersecurity controls, which can be a costly and time-consuming process. And with the upcoming changes for CMMC 2.0, there are new considerations to be addressed.
Whereas other security certifications are more approachable, CMMC is very technical in its documentation and nature. There are many mentions of specifications that require some fastidious attention, such as NIST SP 800-171 versus NIST SP 800-172 and which specification is required for what levels in both V1.0 and V2.0. Some V1.0 security controls have been dropped in V2.0, such as the “Delta 20” controls, which were added in 2021, but have since been removed in V2.0
In other words, there’s a lot going on and a lot to keep in mind.
It’s best to keep close tabs on the CMMC spec, especially as it evolves with the 2.0 roadmap. Consider working with a knowledgeable specialist who can shepherd your organization through the process.
As for misconceptions, some people mistakenly believe that CMMC is only required for government contractors. This is untrue; CMMC is required for any organization working with CUI. Furthermore, CMMC is a continuous certification, not a one-and-done, which means every three years you’ll need to re-certify. And as it goes for nearly every cybersecurity framework, CMMC is not a silver bullet for your information security needs. Getting certified is a big step in the right direction, but it is not a guarantee for protecting your organization from attack. You must remain vigilant.
Use automation to track and manage your CMMC controls
Depending on the level of your CMMC certification, you could be managing hundreds of security controls across thousands of pieces of infrastructure. This is far too much for even a dedicated team to track. You are much better off employing an automated tool to track, manage, and remediate your compliance needs. ComplianceCow is a rule-based, no-/low-/high-code platform with advanced ChatOps capabilities. Manage your compliance directly from Slack or Teams with human-readable rulesets and flexible constructs. We are the only tool offering management of 100% of your security controls. ComplianceCow empowers you to achieve your security goals and make governance actionable.
