In the world of GRC (which means Governance, Risk, and Compliance), it’s super important to keep everything organized. We all talk about Continuous Control Monitoring and Automated Evidence gathering. Yet, there are so many rules and pieces of proof that it gets really confusing to figure out what they mean and what to do with them.
Sometimes, a small problem like a medium vulnerability might seem okay on its own. But when you add it to other similar issues, like admins without extra security measures, it can become a bigger concern. Connecting these findings helps to understand the full scope of the problem and make better decisions.
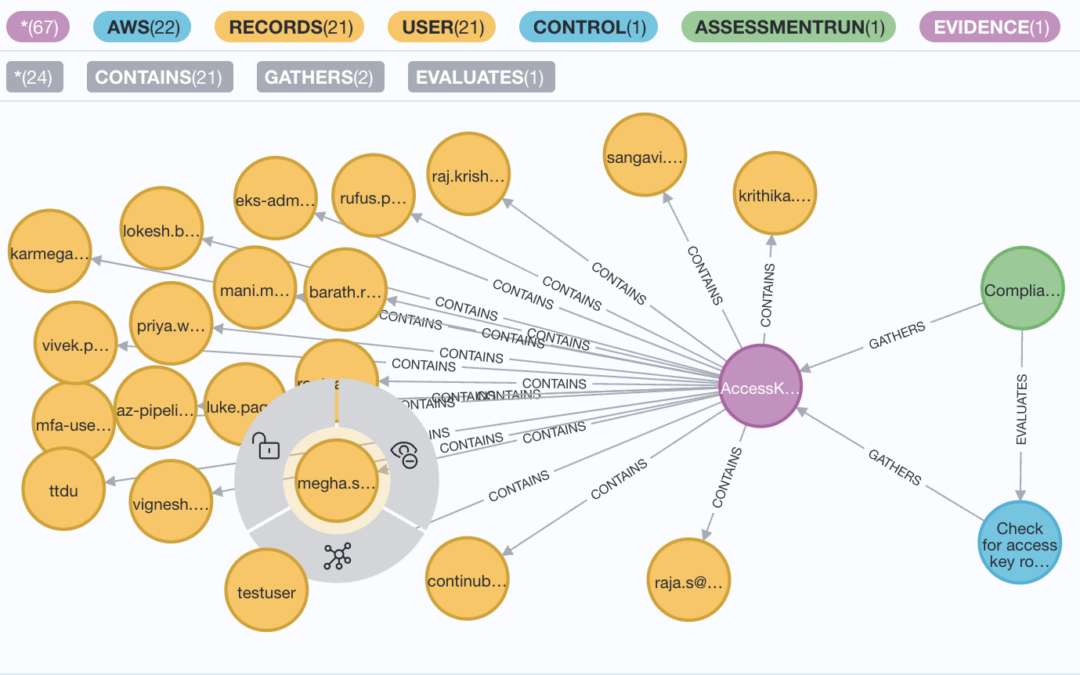
One way to approach this problem is by converting regulatory requirements into a graph model. Let’s break down how this works:
Establishing the Model Structure: Firstly, we organize regulatory frameworks into assessments. Each assessment encompasses controls, which in turn encompass evidence. Evidence, in this context, comprises individual records. These records can function as either actors or resources, with potential correlations between various resources.
After the initial step of defining the schema, we can define the relationships between these schemas, incorporating metadata and essential attributes.
Asking intriguing Inquiries: After setting up the schema, we can utilize the graph model to address interesting questions and derive insights. For example:
- What is the count of Non-Compliant users?
- Within the Non-Compliant user group, how many are Admin users?
- Among Non-Compliant Admin users, how many lack Multi-Factor Authentication (MFA)?
- Of the Non-Compliant Admin users without MFA, how many retain system access post-termination?
- How many users utilized credentials post termination?
Another example below:
- How many Kubernetes pods are configured without dropping the NET_RAW capability, which grants user access to the Linux system?
- Are these pods deployed on virtual machines that are publicly exposed to the internet?
- Have the virtual machines been properly configured with firewall rules to regulate network traffic?
- Do any unauthorized users possess write access to these firewall rules?
Integration with Natural Language Processing (NLP): Leveraging Natural Language Processing (NLP) on top of the graph model allows users to ask questions in plain English text. The questions are converted into GraphQL queries, and the results are processed through NLP for easy comprehension.
ChatOps Integration: Finally this solution can be integrated with ChatOps platforms like Slack, Teams, or Webex. Imagine the power of querying compliance data and getting answers directly through a chatbot interface without logging into any tool.
ComplianceCow offers a comprehensive solution to regulatory compliance challenges. By conducting continuous control monitoring and gathering evidence, it ensures adherence to regulatory requirements. The conversion of this evidence into a Neo4j graph model provides a visual representation of compliance status and dependencies.
Integration with LLM (Large Language Model) and Slack streamlines the process of querying compliance information. Users can effortlessly ask questions via Slack, Teams, or Webex, receiving prompt and accurate responses from ComplianceCow. This seamless integration enhances accessibility and efficiency in managing compliance tasks, empowering organizations to maintain regulatory compliance effectively.