Security Compliance is Changing. But Are We?
Regulations are growing more complex. IT environments are evolving faster than ever. Yet, many compliance programs are still operating as if systems are static and risks are predictable.
Recently, I sat down with Mosi Platt, an expert in security GRC, compliance automation, and risk management, to discuss how compliance teams need to rethink their approach.
Mosi’s career spans everything from post-Sarbanes-Oxley IT audits to modern cloud security assurance. He’s seen firsthand what works, what doesn’t, and where compliance needs to evolve.
One thing became clear in our conversation: Compliance teams can no longer operate as if their systems are locked down and predictable. The world has moved on.
So, how do we modernize compliance in a world that’s increasingly dynamic? Here are some key takeaways from our discussion.
1. Security Governance is a Myth If the Board Isn’t Involved
Mosi started our conversation sharing how many compliance teams assume security governance is well-defined in their organization. But in reality, Mosi says, governance is often more aspirational than real.
“The way governance is supposed to work is that it comes from the top down,” Mosi said. “If security leaders don’t have direct influence at the board level and if the board isn’t actively evaluating, directing, and monitoring security strategy, then what they’re doing isn’t really governance. It’s just management.”
This disconnect has real consequences for compliance teams. Without clear governance, compliance functions are often left interpreting security mandates on their own, leading to conflicting priorities and reactive processes rather than a cohesive, strategic approach.
If compliance is being forced to fill the governance gap, then it’s operating in damage control mode. That creates friction. Whereas security GRC compliance done well is more of a business enabler.
2. Risk-Based Thinking Has Limits. Compliance Needs a Trust-Based Model
Mosi shared his experience that for years compliance programs have been built around risk reduction. But risk-based models break down in fast-moving environments, especially when dealing with complex systems or AI-driven processes.
“If you’re getting output from a black box, how can you enumerate all the risks?” Mosi asked. “You can’t. But you can define which stakeholders need to trust that system.”
Mosi suggests that instead of trying to list and mitigate every conceivable risk, compliance teams need to ask different questions:
- What do stakeholders need in order to trust that security controls are working?
- How can compliance teams demonstrate assurance, proactively, rather than reacting to issues?
Traditional risk-based approaches assume you can predict failure points and mitigate them. But when dealing with large-scale, hybrid, or proprietary infrastructure, compliance teams must shift toward trust-based assurance, where the focus is on ensuring confidence in security controls, even when risks are unknown.
3. Legacy Compliance Models Were Built for Static Systems. But Constant Change is Today’s Reality
Many compliance programs were designed for an era when IT environments were stable and rarely changed. But today’s enterprises operate in a mix of on-prem, proprietary, hybrid cloud, multi-cloud, and rapidly evolving DevOps environments. Compliance teams haven’t caught up.
“A lot of compliance programs were built in a time when best practice was to avoid updating revenue-generating systems unless absolutely necessary,” Mosi explained. “Now, with DevOps, Agile, and cloud adoption, environments are dynamic. But compliance programs haven’t fully adjusted to that reality.”
This is especially problematic when compliance teams are still operating with old processes. A framework that was designed for annual audit cycles and long-term risk assessments isn’t equipped to handle real-time changes in infrastructure security configurations or emerging vulnerabilities in AI-driven systems.
If compliance continues operating as if systems are locked down and predictable, it will just slow down business and create unnecessary friction with security and engineering teams who are trying to keep up with demands from the business.
4. The Four Quadrants Model. A Smarter Way to Assess Compliance Programs
Mosi has developed a four-quadrant model to help compliance teams determine whether their existing program is still fit for purpose. It considers two key factors:
- Stakeholder Engagement – Are external stakeholders friendly or adversarial toward the compliance program?
- Environmental Stability – Is the IT environment static or dynamic?
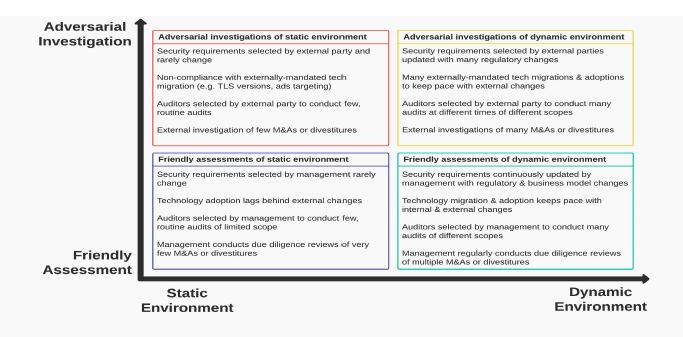
“A lot of compliance programs were built around static environments, where the goal was to avoid change,” Mosi said. “But now, we’re dealing with dynamic environments, multi-cloud compliance requirements, and global regulations. If your compliance program isn’t adapting, it’s creating unnecessary risk.”
A compliance framework that was designed for a static system with cooperative stakeholders may no longer be effective in a highly dynamic, high-scrutiny environment. Compliance teams need to assess whether their frameworks still make sense. And if they need to evolve, then how to change to increase agility and value to the business?
5. Making the Business Case for Security and Compliance. Without Losing Credibility
Getting buy-in for security compliance initiatives isn’t just about presenting risk data. You need to frame compliance as a business enabler.
Mosi shared a lesson from early in his career when he wrote an audit report so aggressive that it backfired. Instead of prompting action, it put executives on the defensive.
“I had just gotten my CISA certification, and they teach you that the purpose of an audit report is to ‘shock management into action,” Mosi said. “So, I wrote this inflammatory report, and it blew up in my face. The executives felt ambushed.”
That experience taught him a key lesson: lead with truth, not hyperbole. Executives don’t respond well to scare tactics. They want:
- A clear statement of the problem.
- A realistic solution.
- An understanding of how security and compliance creates business value.
If compliance teams want buy-in for automation, investments, or process improvements, they need to frame compliance as a business enabler, not just a regulatory requirement.
6. Compliance Needs to Shift Left. And Become More Integrated with Security and DevOps
One of the biggest challenges for compliance professionals today is playing catch-up with security and engineering teams that have already undergone digital transformation.
“Security compliance needs to follow the same transformation that DevOps went through,” Mosi said. “But that means compliance professionals need to move from being auditors to being active participants in the security process.”
Instead of reviewing evidence after the fact, compliance needs to be built into security processes from the start. That means:
- Automating evidence collection, analysis, and remediation instead of relying on manual audits.
- Embedding compliance requirements into DevOps workflows instead of reacting to security issues after deployment.
The goal? To make compliance an integrated part of security and engineering processes. And make it easier for compliance teams to do more for themselves, without waiting for technical help.
Bridging Insights to Action: How ComplianceCow Helps Compliance Teams
For compliance teams, these shifts are critical:
- From risk-based to trust-based assurance,
- From legacy compliance workflows to modern frameworks
- From manual audits to automation
That’s where ComplianceCow comes in.
🐮 Automates GRC security controls evidence collection, analysis and remediation.
🐮 Works with any GRC platform.
🐮 Supports on-prem, proprietary, hybrid cloud, large & complex systems.
🐮 Supports multiple frameworks simultaneously without adding operational drag.
🐮 Provides clear security insights for both engineers and executives.
No more blind spots or observability gaps. No more chasing for compliance evidence, distracting engineers, or manual updates to ad hoc scripts whenever regulations, controls, or infrastructure changes.
Security compliance is changing. The right tools can help you keep up.
Final Thoughts. Is Your Compliance Program Keeping Up?
Mosi’s experience matches what others have been telling me (check out those conversations, here) Security compliance is no longer about checking boxes. There’s little value-add from that. Today, compliance needs to:
- Build trust with leadership, customers, and regulators.
- “Shift-left” and add value as a second line of security defense.
- Operate quicker to keep up with changing business needs.
The question is: Is your compliance program evolving fast enough?
Let’s make sure it is.
🔹 Want to see if ComplianceCow fits your situation? Book a Demo
🔹 Listen to other conversations with security GRC compliance leads.
